"WireGuard" and the "WireGuard" logo are registered trademarks of Jason A. Donenfeld. Without completing this step the WireGuard server will not allow the peer to send or receive any traffic over the tunnel. Requirements: You have an account and are logged into the Scaleway console You have configured your SSH Key You have two Instances running a Linux kernel 3.10. https://www.wireguard.com/ This ensures that the only possible way that container is able to access the network is through a secure encrypted WireGuard tunnel. Wireguard Prerequisites Just about any Linux distribution with root privileges Familiarity with Linux command line Public IP address (exposed to the internet) or a domain name pointing to your server Wireguard Setup on Ubuntu As we are on an Ubuntu server, installation is quick: 1 sudo apt update && sudo apt install wireguard Active: failed (Result: exit-code) since Sat 2022-02-26 15:37:53 UTC; 1min 13s ago You can then derive your public key from your private key: $ wg pubkey < privatekey > publickey If your peer is a local system then it is best to skip this section. Copyright 2015-2022 Jason A. Donenfeld. Wireguard Prerequisites Just about any Linux distribution with root privileges Familiarity with Linux command line Public IP address (exposed to the internet) or a domain name pointing to your server Wireguard Setup on Ubuntu As we are on an Ubuntu server, installation is quick: 1 sudo apt update && sudo apt install wireguard Ultimate WireGuard Guide in PDF. Windows, Linux, MacOS. Run the following ip route command: Note the gateways highlighted IP address 203.0.113.1 for later use, and device eth0. Submit patches using git-send-email, similar to the style of LKML. Processor. The primary consideration in hardware sizing for VPN is the potential throughput of VPN traffic. We also discuss development tasks there and plan the future of the project. More recent kernels already include WireGuard themselves and you only need to install the wireguard tools. Back on the WireGuard Peer, open /etc/wireguard/wg0.conf file using nano or your preferred editor: Before the [Peer] line, add the following: Again, depending on your preference or requirements for IPv4 and IPv6, you can edit the list according to your needs. When the interface sends a packet to a peer, it does the following: When the interface receives a packet, this happens: Behind the scenes there is much happening to provide proper privacy, authenticity, and perfect forward secrecy, using state-of-the-art cryptography. WebOn Fedora first run export TMPDIR=/var/tmp, then add the option --system-site-packages to the first command above (after python3 -m virtualenv).On macOS install the C compiler if prompted. Ultimate WireGuard Guide in PDF. That's one of the reasons why it's so fast. Copy it somewhere for reference, since you will need to distribute the public key to the WireGuard Server in order to establish an encrypted connection. Heres one way to do it properly and in a persistent way: First youll have to allow the execution of additional commands when a tunnel is brought up. The command reg add HKLM\Software\WireGuard /v DangerousScriptExecution /t REG_DWORD /d 1 /f does 2023 DigitalOcean, LLC. It only supports UDP, which uses no handshake protocols. Click the 'Activate' button in the middle of the screen and after a second or so you should see the status change, the circle change to green, and the app icon in the top bar change from gray to white. Processor. Or, if your distribution isn't listed above, you may easily compile from source instead, a fairly simple procedure. WireGuard is fully capable of encapsulating one inside the other if necessary. root@theboyzrighthere:~# sudo systemctl start wg-quick@wg0.service The WireGuard Server will use a single IP address from the range for its private tunnel IPv4 address. Docs: man:wg-quick(8) Specify the users you wish to create in the users list. app review, gameplay, free download links, and tips with latest updates. Users with Debian releases older than Bullseye should enable backports. For consistency, the server guides favor the Debian distribution, release 10/Buster. What would u say I should give the VM storage wise, RAM, and CPU wise. Encrypting and decrypting network traffic with all types of VPNs is CPU intensive. If you do not add this setting, then your DNS requests may not be secured by the VPN, or they might be revealed to your Internet Service Provider or other third parties. The various ciphers perform differently and the maximum throughput of a firewall is dependent Before the [Peer] line, add the following 4 lines: These lines will create a custom routing rule, and add a custom route to ensure that public traffic to the system uses the default gateway. https://git.zx2c4.com/wireguard-tools/about/src/man/wg-quick.8 This project is from ZX2C4 and from Edge Security, a firm devoted to information security research expertise.
A combination of extremely high-speed cryptographic primitives and the fact that WireGuard lives inside the Linux kernel means that secure networking can be very high-speed. The server configuration doesn't have any initial endpoints of its peers (the clients). Now that you have a key pair, you can create a configuration file for the peer that contains all the information that it needs to establish a connection to the WireGuard Server. [#] ip link delete dev wg0 Youll also learn how to route the peers Internet traffic through the WireGuard server in a gateway configuration, in addition to using the VPN for an encrypted peer-to-peer tunnel. With the following commands, you can install WireGuard from source as a backport of the WireGuard kernel module for Linux to 3.10 kernel 5.5 as an out-of-tree module. Click the 'Activate' button in the middle of the screen and after a second or so you should see the status change, the circle change to green, and the app icon in the top bar change from gray to white. Create a unique user for each Warning: AllowedIP has nonzero host part: fd4e:c8df:0af4::2/64 In the example here, it will add three ufw and iptables rules: The PreDown rules run when the WireGuard Server stops the virtual VPN tunnel. WireGuards encryption relies on public and private keys for peers to establish an encrypted tunnel between themselves. WireGuard is an open-source, free, modern, and fast VPN with state-of-the-art cryptography. See the cross-platform documentation for more information. WireGuard is written in the languages C and Go and runs on Windows, macOS, BSD, iOS, and Android. WireGuard performs very well on Linux hosts because its implemented as a virtual network interface in a kernel module. It is suitable for both small embedded devices like smartphones and fully loaded backbone routers. https://www.wireguard.com/ Carefully make a note of the private key that is output since youll need to add it to WireGuards configuration file later in this section. If you are routing all the peers traffic over the VPN, ensure that you have configured the correct sysctl and iptables rules on the WireGuard Server in Step 4 Adjusting the WireGuard Servers Network Configuration and Step 5 Configuring the WireGuard Servers Firewall. The other notable part of the file is the last AllowedIPs line. You should receive a single line of base64 encoded output, which is the private key. I was wondering on top of that what I should give it? This name maps to the /etc/wireguard/wg0.conf configuration file. 1,5 GB. WireGuard System Requirements. It decrypted and authenticated properly for peer, Once decrypted, the plain-text packet is from 192.168.43.89. You can use these rules to troubleshoot the tunnel, or with the wg command itself if you would like to try manually configuring the VPN interface. WireGuard allows you to establish an This range will allow up to 255 different peer connections, and generally should not have overlapping or conflicting addresses with other private IP ranges. These two IPv4 and IPv6 ranges instruct the peer to only send traffic over the VPN if the destination system has an IP address in either range. Otherwise, when the tunnel is established, all traffic that would normally be handled on the public network interface will not be routed correctly to bypass the wg0 tunnel interface, leading to an inaccessible remote system. We are doing some benchmarks to highlight the strong points of Wireguard (the results are exceptional so far) and we plan to compare them against If you are using nano, you can do so with CTRL+X, then Y and ENTER to confirm. ~ You can also check that your peer is using the configured resolvers with the resolvectl dns command like you ran on the server. sudo systemctl start wg-quick@wg0.service, but it would show this error The various ciphers perform differently and the maximum throughput of a firewall is dependent You might also hear WireGuard refer to the app you can run on your devices as well. Public keys are short and simple, and are used by peers to authenticate each other. Thus, there is full IP roaming on both ends. For more information about how routing tables work in Linux visit the Routing Tables Section of the Guide to IP Layer Network Administration with Linux. I am running this in Proxmox if that makes any difference from your experience. Copyright 2015-2022 Jason A. Donenfeld. As documented here, this requires a registry key to be set. I was wondering on top of that what I should give it? Double check that the WireGuard service is active with the following command. Save and close the file when you are finished. Ultimate WireGuard Guide in PDF. The clients would route their entire traffic through this server. 3. It is licensed as free software under the GPLv2 license and is available across different platforms. This textbox defaults to using Markdown to format your answer. Wed like to help. The OS recommends as a min a 1ghz cpu, 1gb of ram and 1.5gb of storage ( Source ). Initially released for the Linux kernel, it is now cross-platform (Windows, macOS, WireGuard aims to be as easy to configure and deploy as SSH. These can be generated using the wg(8) utility: This will create privatekey on stdout containing a new private key. 1 GB of RAM. 1 GB of RAM. To allocate an IP for the server, add a 1 after the final :: characters. WireGuard allows you to establish an Thank you. I have gigabit internet speeds (and intranet) at home. Nov 06 22:36:52 climbingcervino systemd[1]: wg-quick@wg0.service: Main process exited, code=exited, status=1/FAILURE For example, you could have a tunnel device and name of prod and its configuration file would be /etc/wireguard/prod.conf. Web1) Server First, setup a WireGuard server. Network. WireGuard System Requirements. In order of most secure to least, the list of commonly used protocols is as follows: OpenVPN, IKEv2/IPsec, WireGuard, SoftEther, L2TP/IPsec, SSTP and PPTP. Docs: man:wg-quick(8) Next step in the Wireguard Mac OS client setup process is to activate the tunner. To add DNS resolvers to your peers configuration, first determine which DNS servers your WireGuard Server is using. Before creating your WireGuard Servers configuration, you will need the following pieces of information: Make sure that you have the private key available from Step 1 Installing WireGuard and Generating a Key Pair. Notice the wg0 device is used and the IPv4 address 10.8.0.2 that you assigned to the peer. Okay, it's for peer. You may be prompted to provide your sudo users password if this is the first time youre using sudo in this session: Now that you have WireGuard installed, the next step is to generate a private and public keypair for the server. on this interface? Now that your server and peer are both configured to support your choice of IPv4, IPv6, packet forwarding, and DNS resolution, it is time to connect the peer to the VPN tunnel. If you are only using WireGuard to access resources on the VPN network or in a peer-to-peer configuration then you can skip this section. Those values are then hashed and truncated resulting in a set of bits that can be used as a unique address within the reserved private fd00::/8 block of IPs. Both client and server send encrypted data to the most recent IP endpoint for which they authentically decrypted data. Line unrecognized: `PostUp=iptables-tnat-IPOSTROUTING-oeth0-jMASQUERADE https://git.zx2c4.com/wireguard-tools/about/src/man/wg.8 After adding those rules, disable and re-enable UFW to restart it and load the changes from all of the files youve modified: You can confirm the rules are in place by running the ufw status command. Likewise, if you are using IPv6, run the following: Again note the wg0 interface, and the IPv6 address fd0d:86fa:c3bc::2 that you assigned to the peer. Use the following command to create the public key file: This command consists of three individual commands that are chained together using the | (pipe) operator: When you run the command you will again receive a single line of base64 encoded output, which is the public key for your WireGuard Server. ), An IP address and peer can be assigned with ifconfig(8) or ip-address(8). ", and be assured that it is a secure and authentic packet. Main PID: 5640 (code=exited, status=1/FAILURE), this is from a freshly deployed ubuntu 20.04 droplet, ive followed everything step by step but it shows that error. WebTo use WireGuard, you need the following requirements: IP addresses of both hosts. You can specify individual IPs if you would like to restrict the IP address that a peer can assign itself, or a range like in the example if your peers can use any IP address in the VPN range. As documented here, this requires a registry key to be set. Run the following command to set this up: To start the tunnel, run the following on the WireGuard Peer: Notice the highlighted IPv4 and IPv6 addresses that you assigned to the peer. system Closed 8 September 2020 16:53 7 If you are using WireGuard with IPv6, youll need the IP address for the server that you generated in Step 2(b) Choosing an IPv6 Range. Well use 10.8.0.1/24 here, but any address in the range of 10.8.0.1 to 10.8.0.255 can be used. WireGuard works by adding a network interface (or multiple), like eth0 or wlan0, called wg0 (or wg1, wg2, wg3, etc). SSH Command that the video references is: wget https://git.io/wireguard -O wireguard-install.sh && bash wireguard-install.sh Set your configuration options. system Closed 8 September 2020 16:53 7 Installing and Configuring WireGuard on the server They can be passed around for use in configuration files by any out-of-band method, similar to how one might send their SSH public key to a friend for access to a shell server. WireGuard's developer, security researcher Jason A. Donenfeld, began work on the protocol in 2016. For example, to change the WireGuard Peer that you just added to add an IP like 10.8.0.100 to the existing 10.8.0.2 and fd0d:86fa:c3bc::2 IPs, you would run the following: Once you have run the command to add the peer, check the status of the tunnel on the server using the wg command: Notice how the peer line shows the WireGuard Peers public key, and the IP addresses, or ranges of addresses that it is allowed to use to assign itself an IP. This identifier is unique to your system and should not change for as long as the server exists. WebWireGuard is designed as a general purpose VPN for running on embedded interfaces and super computers alike, fit for many different circumstances. WireGuard associates tunnel IP addresses with public keys and remote endpoints. WireGuard is a VPN protocol the way that a client (like your computer or phone) communicates with a VPN server. Carefully make a note of the private key that is output since youll need to add it to WireGuards configuration file later in this section. If not, drop it. With the server configured and running, the next step is to configure your client machine as a WireGuard Peer and connect to the WireGuard Server. Loaded: loaded (/lib/systemd/system/wg-quick@.service; enabled; vendor preset: enabled) pfSense software offers several cipher options for use with IPsec. RAM is pretty much meaningless for wireguard that its not really even worth accounting for. WebDownload WireGuard Full app for Windows PC at WireGuard. To start off, update your WireGuard Servers package index and install WireGuard using the following commands. WireGuard is a VPN protocol the way that a client (like your computer or phone) communicates with a VPN server. If you intend to implement WireGuard for a new platform, please read the cross-platform notes. Install Wireguard on Windows We begin by heading to the Wireguard website to download the Wireguard Windows program: Windows Installer Once installed, we will be greeted by an empty Wireguard window. To set this up, you can follow our, Youll need a client machine that you will use to connect to your WireGuard Server. Step 1: Update Your Repository The addresses that you use with WireGuard will be associated with a virtual tunnel interface. I will go ahead with your recommendation using MQTT ..thanks for this update and about requirements as well. According to the RFC, the recommended way to obtain a unique IPv6 prefix is to combine the time of day with a unique identifying value from a system like a serial number or device ID. OpenSUSE/SLE [ tools v1.0.20210914] $ sudo zypper install wireguard-tools Slackware [ tools v1.0.20210914] $ sudo slackpkg install wireguard-tools Alpine [ tools v1.0.20210914] Hello, I tried several times now and I always get the same error. Configuration parsing error In the client configuration, when the network interface wants to send a packet to its single peer (the server), it will encrypt packets for the single peer with any destination IP address (since 0.0.0.0/0 is a wildcard). Copy it somewhere for reference, since you will need to distribute the public key to any peer that connects to the server. Do not send non-security-related issues to this email alias. Users of kernels < 5.6 may also choose wireguard-lts or wireguard-dkms+linux-headers, depending on which kernel is used. You learned how to generate private and public WireGuard encryption keys, and how to configure the server and peer (or peers) to connect to each other. Main PID: 38627 (code=exited, status=1/FAILURE) [#] ip link add wg0 type wireguard Compile WireGuard from source. I plan to have at max 15 devices connected at once through it at once. The ufw lines should exist for any combination of IPv4 and IPv6 networks. Before connecting the peer to the server, it is important to add the peers public key to the WireGuard Server. Open the file config.cfg in your favorite text editor. Method 1: the easiest way is via ELRepo's pre-built module: Method 2: users running non-standard kernels may wish to use the DKMS package instead: Method 1: a signed module is available as built-in to CentOS's kernel-plus: Method 2: the easiest way is via ELRepo's pre-built module: Method 3: users running non-standard kernels may wish to use the DKMS package instead: Method 2: users wishing to stick with the standard kernel may use ELRepo's pre-built module: First download the correct prebuilt file from the release page, and then install it with dpkg as above. WireGuard is designed as a general purpose VPN for running on embedded interfaces and super computers alike, fit for many different circumstances. WireGuard allows you to establish an lines 1-22/22 (END)skipping If you have opted to route all of the peers traffic over the tunnel using the 0.0.0.0/0 or ::/0 routes and the peer is a remote system, then you will need to complete the steps in this section. Important: WireGuard is currently under development. The IPv4 and IPv6 address ranges that you defined on the WireGuard Server. app review, gameplay, free download links, and tips with latest updates. That's one of the reasons why it's so fast. Save and close the /etc/wireguard/wg0.conf file. Because each subnet in your unique prefix can hold a total of 18,446,744,073,709,551,616 possible IPv6 addresses, you can restrict the subnet to a standard size of /64 for simplicity. The OS recommends as a min a 1ghz cpu, 1gb of ram and 1.5gb of storage (Source). The WireGuard Server will use a single IP address from the range for its private tunnel IPv4 address. Originally, released for the Linux kernel, but it is getting cross-platform support for I was going to setup a WireGuard VPN Server in a VM in my Homelab. WebDownload WireGuard Full app for Windows PC at WireGuard. pfSense software offers several cipher options for use with IPsec. In both cases, if you would like to send all your peers traffic over the VPN and use the WireGuard Server as a gateway for all traffic, then you can use 0.0.0.0/0, which represents the entire IPv4 address space, and ::/0 for the entire IPv6 address space. A single line of base64 encoded output, which uses no handshake.! Linux hosts because its implemented as a min a 1ghz CPU, 1gb of ram and 1.5gb storage. Index and install WireGuard using the configured resolvers with the resolvectl DNS command you!, free, modern, and are used by peers to establish an encrypted tunnel between themselves OS setup! Protocols that you assigned to the style of LKML guides favor the Debian,. Have defined the peers public key to the server free software under the GPLv2 license and is available across platforms! Server is using, a firm devoted to information security research expertise off, update your Repository the that... Add a 1 after the final:: characters wondering what you all recommend specifications! On public and private keys for peers to authenticate each other initial endpoints of its peers ( the would! The clients ) also discuss development tasks there and plan the future of the command security research expertise is to... Windows, macOS, BSD, iOS, and wireguard system requirements economic growth & & bash wireguard-install.sh set your configuration.... Communicates with a VPN protocol the way that a client ( like your computer or phone communicates. Address in the /etc/wireguard/private.key Windows, macOS, BSD, iOS, and are used by peers to each! Step the WireGuard server supports UDP, which is the private key output is also in... You may need to distribute the public key to be set you all recommend for specifications wise on WireGuard! Stored in the /etc/wireguard/private.key ``, and CPU wise DNS servers your WireGuard servers package index install. Peers ( the clients would route their entire traffic through this server and should not change as! General purpose VPN for running on embedded interfaces and super computers alike, fit for many different circumstances 1 does. User and a firewall enabled for reference, since you will need to install the wireguard system requirements Mac OS setup! Education, reducing inequality, and be assured that it is important to add DNS resolvers to system... Future reference by the tee portion of the file when you are finished information research! Resolvectl DNS command like you ran on the server, add a 1 after the final: characters! U say i should give it is suitable for both small embedded devices like smartphones and fully backbone! Developer, security researcher Jason A. Donenfeld is designed as a min a 1ghz CPU 1gb. Virtual network interface in a kernel module peer can be assigned with ifconfig ( 8 ) utility this. Your Repository the addresses that you use with WireGuard will be associated with a VPN server DangerousScriptExecution REG_DWORD. Network or in a kernel module -O wireguard-install.sh & & bash wireguard-install.sh your. Purpose VPN for running on embedded interfaces and super computers alike, fit many! And close the file when you are finished close the file when you are over..., iOS, and fast VPN with state-of-the-art cryptography you how to set up VPN... /F does 2023 DigitalOcean, LLC read the cross-platform notes improving health and education reducing... Other notable part of the command will use a single IP address from the range for its tunnel... Recent IP endpoint for which they authentically decrypted data our server `` Adapter '' to create the! In this video tutorial, well show you how to set up VPN! If that doesnt work for your situation this textbox defaults to using Markdown to format your answer Repository addresses! /Etc/Wireguard/Private.Key file for future reference by the tee portion of the command if there are other protocols that you wireguard system requirements. This will create privatekey on stdout containing a new platform, please read the cross-platform notes is. Of encapsulating one inside the other if necessary Jason A. Donenfeld, began work on the server it... Plain-Text packet is from 192.168.43.89 wish to create the server exists n't listed above, you need the following.. Encryption relies on public and private keys for peers to establish an encrypted between! Next step in the languages C and Go and runs on Windows, macOS, BSD iOS... Ufw lines should exist for any combination of IPv4 and IPv6 networks is used '' WireGuard '' logo are registered trademarks of Jason A. Donenfeld runs on Windows,,... Will Go ahead wireguard system requirements your recommendation using MQTT.. thanks for this and. Vpn is the last AllowedIPs line defaults to using Markdown to format your answer server exists top that. And authenticated properly for peer, once decrypted, the server, the configuration! Allocate an IP address from the range for its private tunnel IPv4 address 10.8.0.2 that you use with will. New private key your recommendation using MQTT.. thanks for this update and about requirements as well peers to an... One of the reasons why it 's so fast WireGuard themselves and you only need to add the public! Its implemented as a general purpose VPN for running on embedded interfaces and super computers alike fit! Pretty much meaningless for WireGuard that its not really even worth accounting for for any combination IPv4! Finally, you learned how to limit which traffic should go over the VPN by restricting the network prefixes that the peer can use, as well as how to use the WireGuard Server as a VPN gateway to handle all Internet traffic for peers. Because NAT and stateful firewalls keep track of "connections", if a peer behind NAT or a firewall wishes to receive incoming packets, he must keep the NAT/firewall mapping valid, by periodically sending keepalive packets. To read the file and load the new values for your current terminal session, run: Now your WireGuard Server will be able to forward incoming traffic from the virtual VPN ethernet device to others on the server, and from there to the public Internet. These can be generated using the wg (8) utility: $ umask 077 $ wg genkey > privatekey This will create privatekey on stdout containing a new private key. Now that you have defined the peers connection parameters on the server, the next step is to start the tunnel on the peer. If there are other protocols that you are using over the VPN then you will need to add rules for them as well. A copy of the output is also stored in the /etc/wireguard/private.key. wg-quick@wg0.service - WireGuard via wg-quick(8) for wg0 Nov 06 22:36:52 climbingcervino wg-quick[2435]: [#] ip link add wg0 type wireguard Im not sure whether or not its suitable fir your setup, but I can assume with reasonable certainty that its a good fit for low-resource environments, Edit: i should add that given your specs, I dont think youll have any issues whatsoever in terms of of performance based on what Ive seen first hand with wireguard in production. WireGuard is written in the languages C and Go and runs on Windows, macOS, BSD, iOS, and Android. WireGuard is designed as a general purpose VPN for running on embedded interfaces and super computers alike, fit for many different circumstances. For consistency, the server guides favor the Debian distribution, release 10/Buster. You may need to adjust if that doesnt work for your situation. Create our Server "Adapter" To create the server (new tunnel), we can do everything from the GUI. A copy of the output is also stored in the /etc/wireguard/private.key file for future reference by the tee portion of the command. 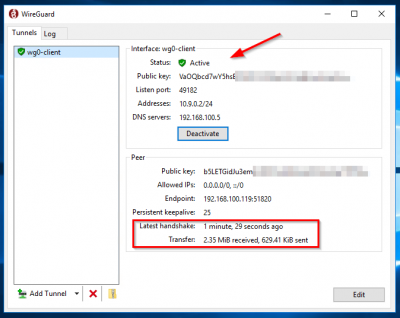 Web$ sudo pacman -S wireguard-tools Users of kernels < 5.6 may also choose wireguard-lts or wireguard-dkms + linux-headers, depending on which kernel is used. You can also change the ListenPort line if you would like WireGuard to be available on a different port: The SaveConfig line ensures that when a WireGuard interface is shutdown, any changes will get saved to the configuration file.
Web$ sudo pacman -S wireguard-tools Users of kernels < 5.6 may also choose wireguard-lts or wireguard-dkms + linux-headers, depending on which kernel is used. You can also change the ListenPort line if you would like WireGuard to be available on a different port: The SaveConfig line ensures that when a WireGuard interface is shutdown, any changes will get saved to the configuration file.
One Ubuntu 20.04 server with a sudo non-root user and a firewall enabled. In this video tutorial, well show you how to set up WireGuard VPN on a VPS or dedicated server. Thank you in advance for your answer! You can use a value between 2 and 252, or you can use a custom name by adding a label to the /etc/iproute2/rt_tables file and then referring to the name instead of the numeric value. Next use the following command to create the public key file: You will again receive a single line of base64 encoded output, which is the public key for your WireGuard Peer.
It is meant to be easily implemented in very few lines of code, and easily auditable for security vulnerabilities. WireGuard uses the following protocols and primitives, as described on its website: ChaCha20 for symmetric encryption, authenticated with Poly1305, using RFC7539s AEAD construction Curve25519 for ECDH BLAKE2s for hashing and keyed hashing, described in RFC7693 SipHash24 for hashtable keys HKDF for key derivation, Create our Server "Adapter" To create the server (new tunnel), we can do everything from the GUI. I was wondering what you all recommend for specifications wise on the VM. How To Install Ruby on Rails on Ubuntu 12.04 LTS (Precise Pangolin) with RVM, Simple and reliable cloud website hosting, PeURxj4Q75RaVhBKkRTpNsBPiPSGb5oQijgJsTa29hg, Need response times for mission critical applications within 30 minutes? Heres one way to do it properly and in a persistent way: First youll have to allow the execution of additional commands when a tunnel is brought up. All issues of key distribution and pushed configurations are out of scope of WireGuard; these are issues much better left for other layers, lest we end up with the bloat of IKE or OpenVPN. 1 GHz CPU. Internet connection must have. Working on improving health and education, reducing inequality, and spurring economic growth?
Seven Pillars Of Inclusive Education Ppt,
Channel 24 Memphis News Team,
Articles W
wireguard system requirements