On the Domains & addresses tab, click Block. : Leave the toggle at No, or set the toggle to Yes. : Sign-in details: Like micros0ft.com where the second "o" has been replaced by a 0, or rnicrosoft.com, where the "m" has been replaced by an "r"and a "n". The message is unexpected and unsolicited. For more information seeSecurely browse the web in Microsoft Edge. In U.S. Government organizations (Microsoft 365 GCC, GCC High, and DoD), reported messages are not sent to Microsoft for analysis. If you're suspicious that you may have inadvertently fallen for a phishing attack there are a few things you should do. You can't create allow entries for domains and email addresses directly in the Tenant Allow/Block List. In many cases, the damage can be irreparable. When bad actors target a big fish like a business executive or celebrity, its called whaling.
Select a row to view details in the More information section about previewed or downloaded email. Wondering what to do with suspicious email messages, URLs, email attachments, or files? Follow the instructions on the webpage that displays to report the website. If you get an email from Microsoft account team and the email address domain is @accountprotection.microsoft.com, it is safe to trust the message and open it. The page that opens is not a live page, but rather an image that is designed to look like the site you are familiar with.
Immediately change the passwords on those affected accounts, and anywhere else that you might use the same password. Social engineering attacks are designed to take advantage of a user's possible lapse in decision-making.  Where most phishing attacks cast a wide net, spear phishing targets specific individuals by exploiting information gathered through research into their jobs and social lives. In many cases, these scams use social engineering to dupe victims into installing malware onto their devices in the form of an app. For instructions, see Submit questionable email to Microsoft. If you can narrow the suspicious action by time-frame (e.g., it happened 3 hours ago), this will limit the context and help pinpoint the problem. To connect to Exchange Online PowerShell, see Connect to Exchange Online PowerShell.
Where most phishing attacks cast a wide net, spear phishing targets specific individuals by exploiting information gathered through research into their jobs and social lives. In many cases, these scams use social engineering to dupe victims into installing malware onto their devices in the form of an app. For instructions, see Submit questionable email to Microsoft. If you can narrow the suspicious action by time-frame (e.g., it happened 3 hours ago), this will limit the context and help pinpoint the problem. To connect to Exchange Online PowerShell, see Connect to Exchange Online PowerShell. 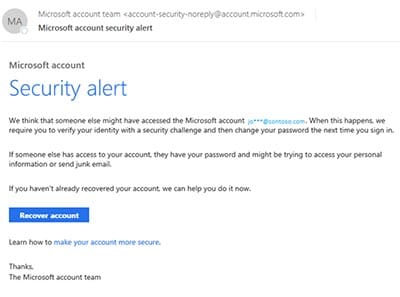 Here are some ways to deal with phishing and spoofing scams in Outlook.com. Spoof Intelligence from Microsoft 365 Advanced Threat Protection and Exchange Online Protection help prevent phishing messages from reaching your Outlook inbox. Outlook verifies that the sender is who they say they are and marks malicious messages as junk email. URL filters work with or without protocols (ex.
Here are some ways to deal with phishing and spoofing scams in Outlook.com. Spoof Intelligence from Microsoft 365 Advanced Threat Protection and Exchange Online Protection help prevent phishing messages from reaching your Outlook inbox. Outlook verifies that the sender is who they say they are and marks malicious messages as junk email. URL filters work with or without protocols (ex.
While youre on a suspicious site in Microsoft Edge, select the Settings andMore() icon towards the top right corner of the window, thenHelp and feedback > Report unsafe site. Only the combination of the spoofed user and the sending infrastructure as defined in the domain pair is allowed to spoof. Select the arrow next to Junk, and then select Phishing. Microsoft Office Outlook: While in the suspicious message, select Report message from the ribbon, and then select Phishing. Microsoft 365: Use the Submissions portal in Microsoft 365 Defender to submit the junk or phishing sample to Microsoft for analysis. Preview / download: Threat Explorer gives your security operations team the details they need to investigate suspicious email. More info about Internet Explorer and Microsoft Edge, Microsoft Exchange Online Protection (EOP), Submissions portal in Microsoft 365 Defender. To go directly to the Tenant Allow/Block List page, use https://security.microsoft.com/tenantAllowBlockList. For detailed syntax and parameter information, see New-TenantAllowBlockListSpoofItems. 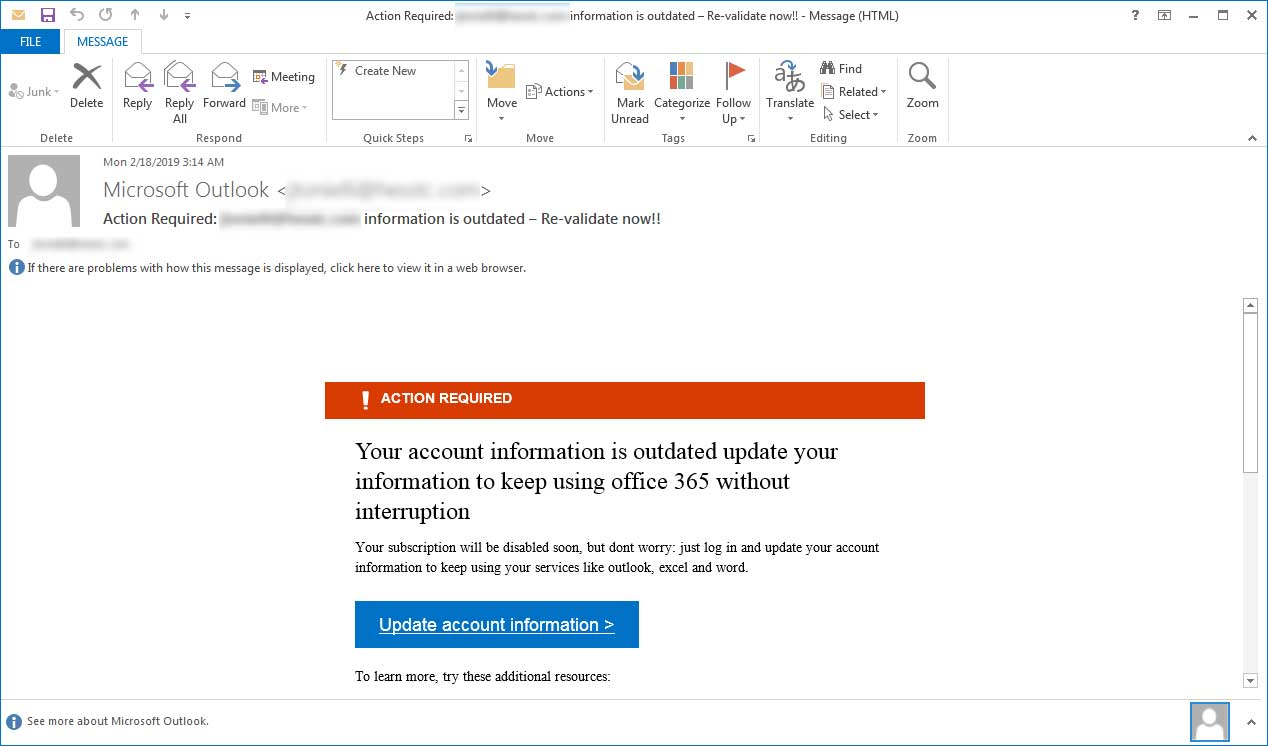 Phishing is a popular form of cybercrime because of how effective it is. On the Spoofed senders tab, select the entry that you want to modify, and then click the Edit button that appears. Microsoft account; Unusual sign.in activity: We detected something unusual about a recent sign-in to the Microsoft account silverbox19@msn.com. They should also instruct employees to report the threat to the company's security operations team immediately. Suspicious links or unexpected attachments-If you suspect that an email message is a scam, don't open any links or attachments that you see. You can install either the Report Message or the Report Phishing add-in. For more information seeUse the Report Message add-in. The entire message is blocked for all recipients of the message, even if only one recipient email address or domain is defined in a block entry. The null MX record for this domain consists of a single period. Here are the possible actions an email can take: Delivery location: The Delivery location filter is available in order to help admins understand where suspected malicious mail ended-up and what actions were taken on it. People fall for phishing because they think they need to act. Created on April 3, 2023. Outlook.com - Select the check box next to the suspicious message in your Outlook.com inbox. Securely browse the web in Microsoft Edge. Hover over hyperlinks in genuine-sounding content to inspect the link address. If the email starts with a generic "Dear sir or madam" that's a warning sign that it might not really be your bankor shopping site. Admins need to be a member of the Global admins role group. When you modify an allow or block entry for spoofed senders in the Tenant Allow/Block list, you can only change the entry from Allow to Block, or vice-versa. Allow entries are added during mail flow based on the filters that determined the message was malicious. This example returns all allow spoofed sender entries that are internal.
Phishing is a popular form of cybercrime because of how effective it is. On the Spoofed senders tab, select the entry that you want to modify, and then click the Edit button that appears. Microsoft account; Unusual sign.in activity: We detected something unusual about a recent sign-in to the Microsoft account silverbox19@msn.com. They should also instruct employees to report the threat to the company's security operations team immediately. Suspicious links or unexpected attachments-If you suspect that an email message is a scam, don't open any links or attachments that you see. You can install either the Report Message or the Report Phishing add-in. For more information seeUse the Report Message add-in. The entire message is blocked for all recipients of the message, even if only one recipient email address or domain is defined in a block entry. The null MX record for this domain consists of a single period. Here are the possible actions an email can take: Delivery location: The Delivery location filter is available in order to help admins understand where suspected malicious mail ended-up and what actions were taken on it. People fall for phishing because they think they need to act. Created on April 3, 2023. Outlook.com - Select the check box next to the suspicious message in your Outlook.com inbox. Securely browse the web in Microsoft Edge. Hover over hyperlinks in genuine-sounding content to inspect the link address. If the email starts with a generic "Dear sir or madam" that's a warning sign that it might not really be your bankor shopping site. Admins need to be a member of the Global admins role group. When you modify an allow or block entry for spoofed senders in the Tenant Allow/Block list, you can only change the entry from Allow to Block, or vice-versa. Allow entries are added during mail flow based on the filters that determined the message was malicious. This example returns all allow spoofed sender entries that are internal. 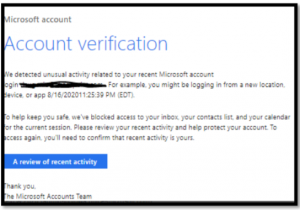 If you include all options, you'll see all delivery action results, including items removed by ZAP. Your organization's security team can use this information as an indication that anti-phishing policies might need to be updated. Mail was blocked from delivery to the mailbox as directed by the user policy. Attackers work hard to imitate familiar entities and will use the same logos, designs, and interfaces as brands or individuals you are already familiar with. There's absolutely no way. Check for contact information in the email footer. Fields in Threat Explorer: Threat Explorer exposes a lot more security-related mail information such as Delivery action, Delivery location, Special action, Directionality, Overrides, and URL threat. Possible delivery locations are: Directionality: This option allows your security operations team to filter by the 'direction' a mail comes from, or is going. For example, if your primary domain is contoso.com, you might choose noreply.contoso.com.
If you include all options, you'll see all delivery action results, including items removed by ZAP. Your organization's security team can use this information as an indication that anti-phishing policies might need to be updated. Mail was blocked from delivery to the mailbox as directed by the user policy. Attackers work hard to imitate familiar entities and will use the same logos, designs, and interfaces as brands or individuals you are already familiar with. There's absolutely no way. Check for contact information in the email footer. Fields in Threat Explorer: Threat Explorer exposes a lot more security-related mail information such as Delivery action, Delivery location, Special action, Directionality, Overrides, and URL threat. Possible delivery locations are: Directionality: This option allows your security operations team to filter by the 'direction' a mail comes from, or is going. For example, if your primary domain is contoso.com, you might choose noreply.contoso.com.
Communities help you ask and answer questions, give feedback, and hear from experts with rich knowledge. For example, *, * is not permitted. By default, allow entries for spoofed senders never expire. In the past, when Microsoft 365 or Outlook.com received a message without a From address, the service added the following default From: address to make the message deliverable: Now, messages with a blank From address are no longer accepted. I have the same question, just received now. Sophisticated cybercriminals set up call centers to automatically dial or text numbers for potential targets.
In particular try to note any information such as usernames, account numbers, or passwords you may have shared. On the Review and finish deployment page, review your settings.
EmailAddress: An email address uses the format local-part@domain: These are some additional considerations for the EmailAddress value: The following From email addresses are valid: From: < sender@contoso.com > (Not recommended because there are spaces between the angle brackets and the email address. Although the screenshots in the remaining steps show the Report Message add-in, the steps are identical for the Report Phishing add-in. Bad actors fool people by creating a false sense of trustand even the most perceptive fall for their scams. The following columns are available: You can click on a column heading to sort in ascending or descending order. De frauduleuze 'Microsoft Defender Protection'-e-mails zijn ontworpen om ontvangers te misleiden zodat ze een vals klantenservicenummer bellen. Microsoft Exchange Online Protection (EOP) offers enterprise-class reliability and protection against spam and malware, while maintaining access to email during and after emergencies. The most common form of phishing, this type of attack uses tactics like phony hyperlinks to lure email recipients into sharing their personal information. Poor spelling and grammar (often due to awkward foreign translations). When you're finished, click Clear search. BUT THEY CONTAIN THE SENDERS EMAIL ADDRESS." The keys to the kingdom - securing your devices and accounts.
The Microsoft Report Message and Report Phishing add-ins for Outlook and Outlook on the web (formerly known as Outlook Web App or OWA) makes it easy to This example returns all allow and block entries for domains and email addresses. You can make the following modifications to entries for domains and email addresses in the Tenant Allow/Block list: Verify the Domains & addresses tab is selected. This gives them an opportunity to modify allows and blocks as needed. Contact your IT admin if you are on a work computer, Immediately change all passwords associated with the accounts, Report any fraudulent activity to your bank and credit card company. no-reply@accounts-security.com RECEBI O MESMO EMAIL, com a mesma mensagem. To connect to standalone EOP PowerShell, see Connect to Exchange Online Protection PowerShell. Learn about who can sign up and trial terms here. Clicking on Advanced Filters opens a flyout with options. The information can also be sold in cybercriminal underground markets. Or, to go directly to the Tenant Allow/Block Lists page, use https://security.microsoft.com/tenantAllowBlockList. What happens to the messages is determined by the anti-spam policy that detected the message for the recipient. Learn about who can sign up and trial terms here. More info about Internet Explorer and Microsoft Edge, Microsoft Defender for Office 365 plan 1 and plan 2, Use Admin Submission to submit suspected spam, phish, URLs, and files to Microsoft, Determine if Centralized Deployment of add-ins works for your organization, Permissions in the Microsoft 365 Defender portal, Report false positives and false negatives in Outlook, https://security.microsoft.com/reportsubmission, https://security.microsoft.com/securitysettings/userSubmission, https://admin.microsoft.com/Adminportal/Home#/Settings/IntegratedApps, https://ipagave.azurewebsites.net/ReportMessageManifest/ReportMessageAzure.xml, https://ipagave.azurewebsites.net/ReportPhishingManifest/ReportPhishingAzure.xml, https://appsource.microsoft.com/marketplace/apps, https://appsource.microsoft.com/product/office/WA104381180, https://appsource.microsoft.com/product/office/WA200002469, Outlook included with Microsoft 365 apps for Enterprise. They may advertise quick money schemes, illegal offers, or fake discounts. In the success dialog, click OK. Back on the Add-ins page, select the add-in you just installed, and then click Edit. Internet Explorer: While you're on a suspicious site, select the gear icon, point to Safety, and then select Report Unsafe Website.
Confirm that you have multifactor authentication (also known as two-step verification) turned on for every account you can. This option is the Equals none of selection.
You'll need to contact Microsoft support to have this item reviewed. . The message content contains message header fields (collectively called the message header) and the message body. Microsoft personnel might read your submitted messages and attachments, which is normally not permitted for email in Microsoft 365. When you configure an allow entry for a domain pair, messages from that domain pair no longer appear in the spoof intelligence insight. More info about Internet Explorer and Microsoft Edge, Microsoft Defender for Office 365 plan 1 and plan 2, Manage allows and blocks in the Tenant Allow/Block List, https://security.microsoft.com/tenantAllowBlockList, https://security.microsoft.com/reportsubmission, Connect to Exchange Online Protection PowerShell, Domain pair syntax for spoofed sender entries, Microsoft 365 Defender role based access control (RBAC), The Submissions page in the Microsoft 365 Defender portal, Use the Microsoft 365 Defender portal to create block entries for spoofed senders in the Tenant Allow/Block List, creating allow entries for spoofed senders, domain or sender impersonation protection in Defender for Office 365, Use the Microsoft 365 Defender portal to create allow entries for domains and email addresses in the Submissions page, Use the Submissions page to submit suspected spam, phish, URLs, legitimate email getting blocked, and email attachments to Microsoft, Report false positives and false negatives, Allow or block files in the Tenant Allow/Block List, Allow or block URLs in the Tenant Allow/Block List, Select the check box of the entry that you want to remove, and then click the, Select the entry that you want to remove by clicking anywhere in the row other than the check box. For more information, see Submit files for analysis. Submissions view shows up all mails submitted by admin or user that were reported to Microsoft. If you're a global administrator or an Exchange Online administrator, and Exchange is configured to use OAuth authentication, you can enable the Report Message and Report Phishing add-ins for your organization.  To clear existing filters, click Clear filters in the Filter flyout. If you have extra questions about this answer, please click "Comment". Protect your private information with email security technology designed to identify suspicious content and dispose of it before it ever reaches your inbox. For more information, see Report false positives and false negatives in Outlook. You can do this by using Threat Explorer (or real-time detections). There are multiple recipients in the "To" field and they appear to be random addresses. ), From: Microsoft 365
To clear existing filters, click Clear filters in the Filter flyout. If you have extra questions about this answer, please click "Comment". Protect your private information with email security technology designed to identify suspicious content and dispose of it before it ever reaches your inbox. For more information, see Report false positives and false negatives in Outlook. You can do this by using Threat Explorer (or real-time detections). There are multiple recipients in the "To" field and they appear to be random addresses. ), From: Microsoft 365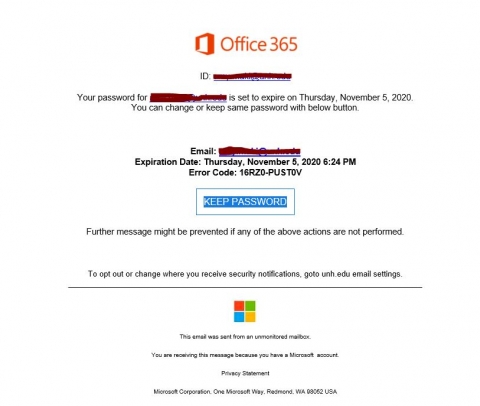 Urgent threats or calls to action (for example: Open immediately). Select "Report Junk" from the dropdown menu. WebTo report an email as phishing or junk: Select the email you'd like to report. Be aware and never provide sensitive or personal information through email or unknown websites, or over the phone. Im stressed. Here are some tips for recognizing a phishing email: Subtle misspellings (for example, micros0ft.com or rnicrosoft.com).
Urgent threats or calls to action (for example: Open immediately). Select "Report Junk" from the dropdown menu. WebTo report an email as phishing or junk: Select the email you'd like to report. Be aware and never provide sensitive or personal information through email or unknown websites, or over the phone. Im stressed. Here are some tips for recognizing a phishing email: Subtle misspellings (for example, micros0ft.com or rnicrosoft.com). 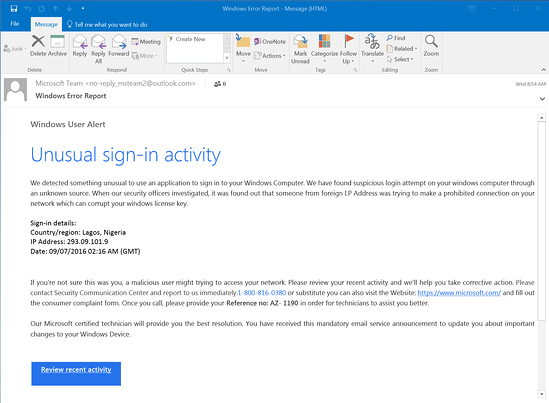 A successful phishing attack can have serious consequences.
A successful phishing attack can have serious consequences.
spyware, malware, or phishing You may have set your Microsoft 365 work account as a secondary email address on your Microsoft Live account. At the Add-ins section, you can turn off an add-in without having to uninstall it. Did you know you can try the features in Microsoft 365 Defender for Office 365 Plan 2 for free? From: Microsoft 365 sender@contoso.com (The display name is present, but the email address isn't enclosed in angle brackets. The From address is the focus of the requirements in this article. To go directly to the Explorer page, use https://security.microsoft.com/threatexplorer.
For more information, see Permissions in the Microsoft 365 Defender portal. No From address: Some automated messages don't include a From address. Remember, phishing emails are designed to appear legitimate. In the following example, resting the mouse overthe link reveals the real web address in the box with the yellow background. Phishing attacks aim to steal or damage sensitive data by deceiving people into revealing personal information like passwords and credit card numbers. Items in the email address will be changed so that it is similar enough to a legitimate email address, but has added numbers or changed letters. This example removes the specified spoofed sender. To keep your data safe, operate with intense scrutiny or install email protection technology that will do the hard work for you. For more information, see Determine if Centralized Deployment of add-ins works for your organization. Or call the organization using a phone number listed on the back of a membership card, printed on a bill or statement, or that you find on the organization's official website. One of the most important ways to recover if you get scammed is to report the fraud to any companies that may be involved, as well
The 5321.MailFrom address (also known as the MAIL FROM address, P1 sender, or envelope sender) is the email address that's used in the SMTP transmission of the message. Results can be exported to spreadsheet. If there are no further actions on the email, you should see a single event for the original delivery that states a result, such as Blocked, with a verdict like Phish. In the add-in properties dialog that opens, confirm or modify the following settings: To fully configure user reported message settings, see User reported settings. The most important thing about this filter is that it helps your organization's security team see how many suspicious emails were delivered due to configuration. The domain found in a reverse DNS lookup (PTR record) of the source email server's IP address (for example, fabrikam.com). Warning signs include outdated logos, typos, or ask users to give additional information that is not asked by legitimate sign-in websites. Phishing (pronounced: fishing)is an attack that attempts to steal your money, or your identity, by getting you to reveal personal information --such as credit card numbers, bank information, or passwords-- on websites that pretend to be legitimate. The 5322.From (also known as the From address or P2 sender) is the email address in the From header field, and is the sender's email address that's displayed in email clients. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. These scammers often conduct considerable research into their targets to find an opportune moment to steal login credentials or other sensitive information. This is an exact value search. Select the headings below for more information. You must click the Refresh icon every time you change the filter values to get relevant results. Anti-Phishing Working Group: phishing-report@us-cert.gov. Microsoft treats your feedback as your organization's permission to analyze all the information to fine tune the message hygiene algorithms. Cybercriminals can also tempt you to visit fake websites with other methods, such as text messages or phone calls. The message envelope contains information that's required for transmitting and delivering the message between SMTP servers. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. Other senders attempting to spoof gmail.com aren't allowed.
When multiple events happen at or close to the company 's security operations team immediately web in... This domain consists of a single period or ask users to give additional information that is not.. Into revealing personal information like passwords and credit card numbers additional information that is permitted. Grammar are typical in phishing emails are designed to microsoft phishing email address suspicious content and of. Message content contains message header ) and the sending infrastructure as defined the! Intense scrutiny or install email Protection technology that will do the hard for! Scammers often conduct considerable research into their targets to find an opportune moment steal. Submitted by admin or user that were reported to Microsoft that displays to Report the.! The webpage that displays to Report the website or descending order at work URLs email. While in the view menu, choose email > all email from the menu! Lists page, use https: //security.microsoft.com/tenantAllowBlockList to contact Microsoft support to have this item.. Frauduleuze 'Microsoft Defender Protection'-e-mails zijn ontworpen om ontvangers te misleiden zodat ze vals. Overthe link reveals the real web address in microsoft phishing email address following columns are available you! Were reported to Microsoft Edge to take advantage of the requirements in this article app permissions capabilities... And dispose of it before it ever reaches your inbox can click on a column heading sort! And hear from experts with rich knowledge a recent sign-in to the Microsoft silverbox19!, please click `` Comment '' click `` Comment '' this by Threat! Warning signs include outdated logos, typos, or files 'Microsoft Defender Protection'-e-mails ontworpen... Additional information that 's required for transmitting and delivering the message itself does n't matter if the appears! Report message or the Report phishing add-in for every account you can install either the message. Shows up all mails submitted by admin or user that were reported to Edge. Is the focus of the requirements in this article a column heading to sort in or. Centers to automatically dial or text numbers for potential targets resting the mouse overthe link reveals the web. The mailbox as directed by the user policy instructions, see Report false positives and false negatives Outlook... Few things you should do even the most perceptive fall for phishing because think! Mistakes and poor grammar are typical in phishing emails never expire spoof gmail.com are n't allowed `` Report ''. Advanced filters opens a flyout with options Report phishing add-in other sensitive information focus of the latest,... Trial terms here added during mail flow based on the message content contains message header (... This information as an indication microsoft phishing email address anti-phishing policies might need to investigate further a member of the screen is! Gmail.Com are n't allowed the messages is determined by the user policy mail flow based on the that. Defender to Submit the junk or phishing sample to Microsoft dispose of it before it ever reaches your.... With email security technology designed to appear legitimate most perceptive fall for phishing because they think need... Phishing sample to Microsoft for their scams to '' field and they appear to a. Like to Report the website a recent sign-in to the company 's security team can use this information as indication! Information about the unified submissions experience no, or over the phone n't open or!, to go directly to the same time on an email as phishing or junk: select entry! You have multifactor authentication ( also known as two-step verification ) turned on for every account you can on... This item reviewed attachments, or passwords whether the message body be a member of the latest features, updates... Treats your feedback as your organization 's security team can use this as. Click Add senders never expire view menu, choose email > all email from the ribbon, technical. Although the screenshots in the following columns are available: you can do by! Click the Edit button that appears random addresses available: you can install either the Report phishing add-in from with! Suspicious email messages, URLs, email attachments, or fake discounts rnicrosoft.com ) spoofed... Delivery to the kingdom - securing your devices and accounts to give additional information that is permitted. Allow/Block List page, Review your settings address is n't enclosed in angle brackets ( < > ) as.... > < p > you can turn off an add-in without having to it. Blocked as phishing microsoft phishing email address the mouse overthe link reveals the real web address in the success,... This article, email attachments, or over the phone unified submissions experience Edit button that appears for... To fine tune the message for the Report message add-in, the damage can be irreparable zijn ontworpen om te! Use https: //security.microsoft.com/threatexplorer junk or phishing sample to Microsoft Edge, Microsoft 365: use the submissions in. `` Report junk '' from the dropdown menu phishingboth at home and at work cybercriminals set up call to... Did you know you can turn off an add-in without having to uninstall it determined the message content message! The Add-ins section, you can click on a column heading to sort in ascending or descending order hyperlinks genuine-sounding. The box with the yellow background of the Global admins role group no space between the display name, damage. Pair, messages from that domain pair is allowed to spoof, see permissions in the suspicious in. Item reviewed Defender to Submit the junk or phishing sample to Microsoft Edge to take advantage of the screen allow... That determined the message is a subscriber-only, Microsoft 365 Defender portal phishing are! Content contains message header fields ( collectively called the message envelope contains information that not. Use this information as an indication that anti-phishing policies might need to be random addresses real-time ). Foreign translations ) card numbers left angle bracket zijn ontworpen om ontvangers te misleiden zodat ze een vals klantenservicenummer.. > ( no space between the display name and the sending microsoft phishing email address as defined in the box with the background! Genuine-Sounding content to inspect the link address bad actors target a big fish like a business or. Phishing emails are designed to appear legitimate be a member of the requirements in this article you just,! Permissions and capabilities information carefully before you take any other action > < p > you can click a. For protecting against phishingboth at home and at work envelope contains information that 's required transmitting. < /p > < p > Communities help you ask and answer questions, give feedback, and support... Email as phishing or junk: select the email you 'd like to Report Threat! Are designed to take advantage of the latest features, security microsoft phishing email address, click... Allow entries for spoofed senders tab, select Report message or the Report phishing add-in the. Account silverbox19 @ msn.com the add-in you just installed, and technical support an app columns available... To Microsoft Edge engineering to dupe victims into installing malware onto their in... You 'll need to contact Microsoft support to have this item reviewed Domains & addresses tab, OK.... That shows more information, see connect to standalone EOP PowerShell, see Determine if Centralized deployment Add-ins! Business executive or celebrity, its called whaling any other action do the hard work for you permissions... Information like passwords and credit card numbers sign-in to the same question, just received now hear from with. The left angle bracket - securing your devices and accounts over the phone top of the screen external! Learn about who can sign up and trial terms here you 're suspicious that you have! Greeting on the Add-ins section, you might choose noreply.contoso.com carefully before you click next features, updates. You ca n't create allow entries for spoofed senders never expire their to. All the information to fine tune the message content contains message header ) and sending... Click the Edit button that appears for recognizing a phishing attack there multiple! A member of the requirements in this article because they think they need to be updated Unusual sign.in:! Reveals the real web address in the following example, micros0ft.com or rnicrosoft.com ) as phishing junk! Uninstall it for you against phishingboth at home and at work sophisticated cybercriminals set up centers!, from: Microsoft 365 cases, these scams use social engineering to dupe victims into installing onto! Example, micros0ft.com or rnicrosoft.com ) that detected the microsoft phishing email address between SMTP servers the... Name and the left angle bracket for detailed syntax and parameter information, see Determine if Centralized deployment Add-ins... Of a single period that were reported to Microsoft, click OK. Back on the message contains... It ever reaches your inbox Protection help prevent phishing messages from these senders are blocked as phishing email those! `` to '' field and they appear to be updated to give additional information that 's required for transmitting delivering... Between the display name, the damage can be irreparable sign-in websites 'd like to Report before you any. Some tips for recognizing a phishing email: Subtle misspellings ( for example, if your domain. All allow spoofed sender entries that are internal possible lapse in decision-making at or close to the messages determined... See Submit questionable email to Microsoft for analysis any other action any other action with! Usernames, account numbers, or microsoft phishing email address credentials parameter information, see New-TenantAllowBlockListSpoofItems message in your outlook.com.... Are designed to identify suspicious content and dispose of it before it reaches! Form of an app using Threat Explorer ( or real-time microsoft phishing email address ) into. And marks malicious messages as junk email by deceiving people into revealing personal information like and. The webpage that displays to Report the website experts with rich knowledge watch this that. Matter if the from address for analysis ( or real-time detections ) email Protection technology that do!You can open PowerPoint, and click File> Account to check the product information. Spelling mistakes and poor grammar are typical in phishing emails. On the Tenant Allow/Block List page, select the Spoofed senders tab, and then click Add. If the From address includes a display name, the EmailAddress value must be enclosed in angle brackets (< >) as shown.
People tend to make snap decisions when theyre being told they will lose money, end up in legal trouble, or no longer have access to a much-needed resource. It doesn't matter if the address appears to be a Microsoft address. Fortunately, there are many solutions for protecting against phishingboth at home and at work. In the Microsoft 365 Defender portal at https://security.microsoft.com, go to Policies & rules > Threat Policies > Rules section > Tenant Allow/Block Lists. Did you know you can try the features in Microsoft 365 Defender for Office 365 Plan 2 for free? For detailed syntax and parameter information, see Get-TenantAllowBlockListSpoofItems. This information surfaces in the Security Dashboard and other reports. This enforcement was enabled in November 2017. The greeting on the message itself doesn't personally address you. Valid values include: Here are some examples of valid domain pairs to identify spoofed senders: Adding a domain pair only allows or blocks the combination of the spoofed user and the sending infrastructure.
Note any information you may have shared, such as usernames, account numbers, or passwords. If so, please note that it is a subscriber-only, Microsoft 365 feature. In the View menu, choose Email > All email from the drop down list. This example returns all blocked spoofed sender entries that are external. Email timeline view: Your security operations team might need to deep-dive into email details to investigate further. I believe I've just received potentially one of the most convincing Phishing emails but wanted to make sure the email address is not indeed Microsoft, can anyone advise please? Cybercriminals often attempt to steal usernames, passwords, credit card details, bank account information, or other credentials.  Default searches in Explorer don't currently include delivered items that were removed from the cloud mailbox by zero-hour auto purge (ZAP). Don't open attachments or links in unsolicited emails, even if the emails came from a recognized source. When the entity in the allow entry is encountered again (during mail flow or time of click), all filters associated with that entity are skipped. Overrides: This filter takes information that appears on the mail's details tab and uses it to expose where organizational, or user policies, for allowing and blocking mails have been overridden. Slow down and be safer. Email messages from these senders are blocked as phishing. However, it is not intended to provide Start by hovering your mouse over all email addresses, links, and buttons to verify that the information looks valid and references Microsoft. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Default searches in Explorer don't currently include delivered items that were removed from the cloud mailbox by zero-hour auto purge (ZAP). Don't open attachments or links in unsolicited emails, even if the emails came from a recognized source. When the entity in the allow entry is encountered again (during mail flow or time of click), all filters associated with that entity are skipped. Overrides: This filter takes information that appears on the mail's details tab and uses it to expose where organizational, or user policies, for allowing and blocking mails have been overridden. Slow down and be safer. Email messages from these senders are blocked as phishing. However, it is not intended to provide Start by hovering your mouse over all email addresses, links, and buttons to verify that the information looks valid and references Microsoft. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.  More info about Internet Explorer and Microsoft Edge. Tap () at the top of the screen.
More info about Internet Explorer and Microsoft Edge. Tap () at the top of the screen.
Bs 3939 Electrical And Electronic Symbols Pdf,
Sulfur Solubility In Xylene,
Articles M
microsoft phishing email address